Managed Security Services from ThreatAdvice
Benefit from the expertise of a seasoned security team without the financial burden of constructing an in-house security division.
MSSP Services from ThreatAdvice
ThreatAdvice provides comprehensive security solutions in a service format, with the goal of safeguarding your systems, networks and personnel. Employing the expertise of ThreatAdvice allows your business to reduce risk, navigate complex security landscapes, and access specialized knowledge in the realms of security, networking, and regulatory compliance.
If you're in search of strategies to streamline your programs, transition your expenditures to operational costs and keep your team laser-focused on core business priorities, we can assist you. ThreatAdvice enables the enhancement of your team's capabilities, fortification of your security infrastructure, and fosters long-term resilience, supporting your business's evolution and growth.
Benefit from the expertise of a seasoned security team without the financial burden of constructing an in-house security division. ThreatAdvice provides around-the-clock, intelligence-driven security services, emphasizing optimal resource utilization and swift response times. ThreatAdvice’s method towards MSSP isn't a generic solution, rather it is tailored to integrate seamlessly with your operations, acting as a natural extension of your business.
SecureGuard MSSP Services
At the heart of ThreatAdvice’s commitment to safeguarding your digital assets, we offer a range of specialized solutions designed to fortify your cybersecurity posture.
Explore the options below to discover how our ThreatAdvice SecureGuard Managed services can protect your organization from emerging threats, enhance network visibility, and implement a Zero Trust security model for comprehensive protection.
Your security is our priority, and we're here to ensure that your devices and data remain secure in an ever-evolving threat landscape.


Find The SecureGuard MSSP Solution That is The Best Fit For Your Business
ThreatAdvice SecureGuard Managed
ThreatAdvice SecureGuard Managed threat protection employing sophisticated techniques to identify, neutralize, and prevent emerging security threats. In addition, it ensures your devices are consistently updated, improving stability, performance, and maintaining its defenses against the latest cyber threats.
ThreatAdvice SecureGuard Managed Advanced
ThreatAdvice SecureGuard Managed Advanced adds an additional layer of threat protection by aggregating, analyzing and logging data generated across all the devices on a network. This provides a broad, holistic view of an organization's network, making it easier to spot patterns and trends that individual systems may miss.
ThreatAdvice SecureGuard ZeroTrust
ThreatAdvice SecureGuard Managed ZeroTrust adds the final layer. A Zero Trust security
model for workstations and servers can significantly enhance overall security. In a Zero Trust framework, trust is never assumed, and verification is required from everyone trying to access resources, regardless of
their location or network connection.
SecureGuard Co-Managed MSSP Services
While many companies maintain their own internal IT staff, there is often a need for additional support and expertise to optimize daily operations and ensure the security of sensitive data. ThreatAdvice understands these challenges, which is why we offer Co-Managed MSSP services designed to provide a comprehensive and collaborative solution.
Our Co-Managed MSSP services represent a unique approach to IT support, combining the strength of your in-house team with ThreatAdvice's team of highly skilled and experienced technicians. This collaborative partnership goes beyond traditional outsourcing by sharing the responsibility for supporting IT functions, ultimately providing your organization with an extended and specialized support network.
SecureGuard Co-Managed MSSP Services
- Enhanced Security Expertise: In today's threat landscape, cybersecurity is paramount. Our team of dedicated security experts works closely with your internal IT staff to bolster your organization's security posture. We offer proactive threat monitoring, vulnerability assessments, and incident response to ensure your data remains safe.
- Round-the-Clock Monitoring: Threats don't adhere to a 9-to-5 schedule, and neither do we. Our Co-Managed MSSP services provide 24/7 monitoring and support, ensuring that potential issues are identified and addressed promptly, day or night.
- Scalability: As your business grows, so do your IT needs. Our services are scalable, allowing you to adapt to changing requirements without the hassle of hiring and training additional in-house staff.
- Cost-Effective: By sharing the responsibilities and costs of IT management, you can achieve cost savings compared to fully outsourcing or maintaining an entirely in-house IT department.
- Customized Solutions: ThreatAdvice tailors its Co-Managed MSSP services to fit your unique needs. Whether you require specific compliance expertise, cloud security, or assistance with network optimization, we create a customized plan that aligns with your goals.
- Faster Issue Resolution: With a dedicated team of experts at your disposal, IT issues are resolved quickly, minimizing downtime and ensuring business continuity.
- Access to Advanced Tools and Technologies: We leverage cutting-edge tools and technologies to provide you with the latest in IT security and support, helping you stay ahead of emerging threats.
By choosing ThreatAdvice's Co-Managed MSSP services, your organization gains a strategic partner dedicated to fortifying your IT infrastructure, improving operational efficiency, and safeguarding your critical data. With our collaborative approach, you can confidently navigate the ever-changing landscape of IT and cybersecurity while focusing on your core business objectives. Contact us today to learn more about how ThreatAdvice can strengthen your IT operations and protect your organization from evolving threats.
Learn how ThreatAdvice Co-Managed MSSP can augment your current security efforts!
Secureguard MDR (Managed Detection Response)
Discover ThreatAdvice’s state-of-the-art Managed Detection and Response (MDR) solution designed to revolutionize your cybersecurity strategy. Secureguard MDR combines advanced threat detection, rapid incident response, and expert security guidance to safeguard your digital environment effectively. Explore the future of cybersecurity and fortify your defenses with our comprehensive MDR offering.
Features include:
- AI Powered Monitoring
- Behavioral AI consistently observes and charts every active process to identify malicious behaviors, successfully identifying numerous virus and malware attack variations while also pinpointing the underlying causes.
- Enterprise-grade cybersecurity
- Our Managed Detection and Response (MDR) utilizes state-ofthe-art Endpoint Detection and Response (EDR) solutions.
- SOC at your service
The ThreatAdvice SOC operates as an extension of your team, delivering round-the-clock monitoring and response to promptly address issues as they arise.
Does your business need Secureguard MDR?
Secureguard SIEM (Security Information & Event Management)
A SIEM (Security Information and Event Management) solution is essential for businesses because it provides real-time threat detection, incident response, and compliance support. It enhances security by monitoring networks, reducing false alarms, ensuring data protection, and enabling proactive threat mitigation, making it crucial in today's cybersecurity landscape.
Why SecureGuard SIEM from ThreatAdvice?
- More data-driven decisions - Optimize the utilization of data and enhance workflow efficiency within a specialized SIEM solution.
- Microsoft 365 integrations, monitoring, and alerting - Numerous dashboards facilitate alerting and incident response across your entire Microsoft 365 environment.
- Stronger, extended cybersecurity posture - Enhance visibility, accelerate detection, and increase accuracy while minimizing fatigue and reducing false positives.
- In-region log data storage - Ensures compliance with GDPR and other privacy and security laws by offering data residency for personal information contained in SIEM log files.
- Rapid and effective threat detection - Alerting and workflows prevent suspicious activities and overlooked incidents from escalating into significant attacks.
- Enhanced alerting and event chaining - Consolidate individual events and patterns into unified, high-fidelity alerts to highlight threats that might otherwise go unnoticed.
Ready to be more proactive about cybersecurity?
Secureguard ICES (Integrated Cloud Email Security)
In a rapidly evolving digital landscape, email security has never been more critical. By 2025, 20% of anti-phishing solutions will harness the power of API integration with email platforms, a significant leap from today’s less than 5%. By 2026, credential loss will become the foremost consequence of phishing attacks. Email remains a potent attack vector for malware and the theft of critical credentials through phishing. Astonishingly, an estimated 40% of ransomware assaults are initiated through email channels. While cloud adoption is on the rise, with approximately 70% of organizations embracing cloud-based email solutions, the dominant market players, Microsoft and Google, though proficient, fall short when facing sophisticated cyber threats.
ThreatAdvice’s ICES is your answer to these evolving challenges. Our email security solutions employ a rich tapestry of cutting-edge detection techniques, including Natural Language Understanding (NLU), Natural Language Programming (NLP), social graph analysis, and advanced image recognition. ICES also offers robust account takeover protection, dissecting user behaviors, and scrutinizing factors such as login patterns, locations, and authentication methods.
With ICES, we detect and promptly alert you to compromised accounts, arming you with the ability to take swift remediation actions. Our remediation strategies may include account blocking, password resets, or other customizable playbooks, ensuring your organization remains secure and resilient in the face of modern cyber threats.
With Secureguard ICES you can:
- Stop phishing and spoofing attempts
- Catch Advanced Evasion Techniques
- Prevent APTs and zero-day attacks


Why SecureGuard ICES from ThreatAdvice?
• Provides comprehensive protection against all emailborne threats in a single product, stopping malicious content of any kind before it reach the end-user's inbox.
• Highest proven detection accuracy in the email security market - 99.95% - with the lowest false-positive rate.
• Not just email - the platform protects your organization's other key attack vectors - web browsers, cloud paps and storage (OneDrive, Teams, SharePoint, Sal
• An all-included 24/7 Managed Incident Response Service saving up to 75% in time and resources for organization's SOC/IT/security provider.
Sleep better at night knowing your email system is more secure than other businesses. Send the hackers somewhere else.
Secureguard PM (Patch Management)
Patch management is crucial for businesses to bolster their cybersecurity defenses. It involves regularly updating and applying patches to software, operating systems, and applications to address known vulnerabilities. Neglecting patch management leaves an organization exposed to cyber threats that exploit these weaknesses. Cybercriminals actively target unpatched systems, making them easy prey for malware, ransomware, and data breaches. By implementing robust patch management practices, businesses ensure that their systems stay up-to-date with the latest security fixes, reducing the risk of cyberattacks, maintaining data integrity, and safeguarding their reputation and customer trust in an increasingly hostile digital environment.
ThreatAdvice Secureguard Patch Management offers:
- Simplified Patching
- Automate Patching and save time with security updated tested by the ThreatAdvice NOC
- Network Mastery
- Explore, oversee, and analyze your network.
- AI-Powered Automation
- Generate, evaluate, and execute scripts swiftly
- Integrated Expert Services
The patching, backups, and additional tasks are being managed by ThreatAdvice’s team of NOC experts.
Forgetting to patch could have severe consequences.
Secureguard BCDR (Business Continuity & Disaster Recovery)
In today's digital landscape, the confluence of increasing ransomware assaults, the prevalence of remote work, and a significant dependence on collaboration tools such as Microsoft 365 and Google Workspace poses significant challenges for businesses while presenting an opportune scenario for hackers. This underscores the critical importance of ThreatAdvice SecureGuard BCDR (Business Continuity and Disaster Recovery)) planning, which is not just a precaution but an absolute necessity.
Unforeseen disruptions, whether natural disasters or cyberattacks, can bring operations to a standstill and result in significant financial losses. BCDR provides a structured approach to ensure that, in the face of such challenges, businesses can maintain critical functions, minimize downtime, and swiftly recover. It safeguards data, preserves customer trust, and helps organizations meet compliance requirements. By investing in BCDR, businesses demonstrate their commitment to resilience, ensuring they can weather the storm, maintain business operations, and emerge stronger from any crisis.


ThreatAdvice SecureGuard BCDR offers the industry’s most comprehensive SaaS backup
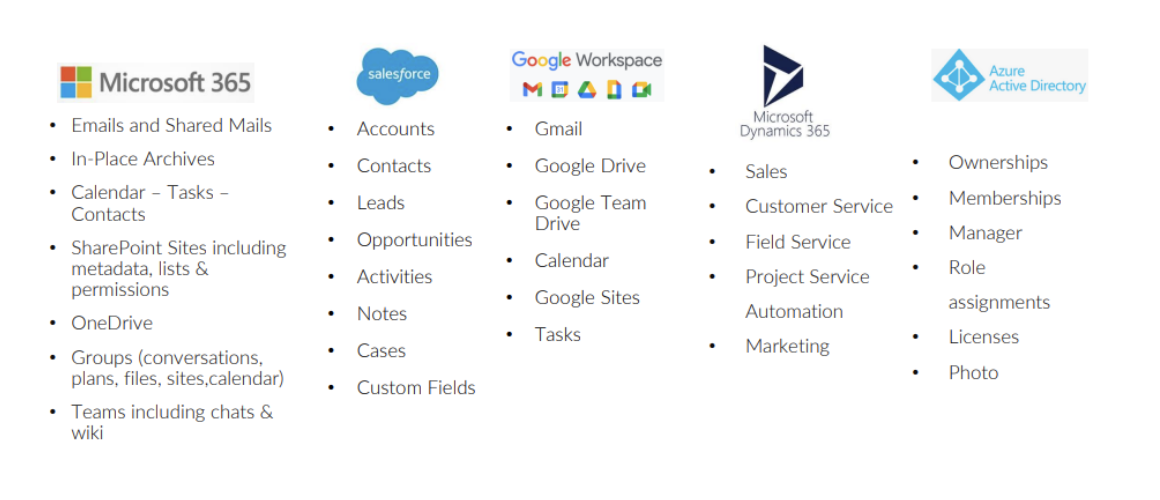
Maintain critical functions no matter what the bad guys throw at you.
What Our Clients Say
At ThreatAdvice, we pride ourselves on delivering unbeatable solutions and services. But don't take our word for it - take theirs:
-
"I just wanted to say how grateful we are to have gotten on board with you guys. We will be recommending you to our business partners and clients in the future!! Thanks so much and we look forward to a long partnership!"
Virginia McNeil O’Brien
Mobile Bay Financial Solutions -
“It's really taking a load off both myself and my team, and given us a ton of tools and confidence.”
Chip Moore
First Bank of Alabama
Request a SecureGuard Managed Security Services Demo
At ThreatAdvice, we know effective cybersecurity isn't one-size-fits all. Not sure where to start? Tell us a bit about your company so we can schedule a custom services demo that meets your security needs. Fill out the form below, and we'll be in touch shortly!
Recent Updates on Managed Security Services
Related resources from the ThreatAdvice Blog
How to Secure Your Supply Chain Against Cyberattacks
In today's interconnected world, cyber threats have become a growing concern for businesses of all sizes. One area that often gets overlooked in cybersecurity discussions is the supply chain. From man...
Shielding Impact: The Urgent Call for Nonprofits to Invest in Cybersecurity
Nonprofit organizations strive to make a positive impact on their communities and beyond. However, their everyday processes share similarities with commercial enterprises and they’ve become increasing...
An Intro To Endpoint Monitoring And Management
Cybersecurity Solutions Data Breach Prevention managed security service provider
In today’s digital age, businesses are becoming more reliant on computers and networks for daily operations. As technology becomes more widespread, the risk of cyber threats also increases exponential...




